Cybersecurity
Protecting Your Systems From Cyber Threats
Securing your Plant Floor
Like other computerized systems, your PLCs, HMIs, and server computers that support them are vulnerable to cyber incidents that interrupt your work and hurt your bottom line. Unlike with IT, an OT cyber incident can lead to damage in the physical world to people or equipment. ACE solves these unique OT cyber challenges with the required cross-domain skills in control systems, networking, IT systems, and integration to develop and implement a cybersecurity strategy for your OT assets. We offer a variety of solutions and services for tackling cybersecurity in new and existing manufacturing environments, at any stage of the project lifecycle.
Technology Partners
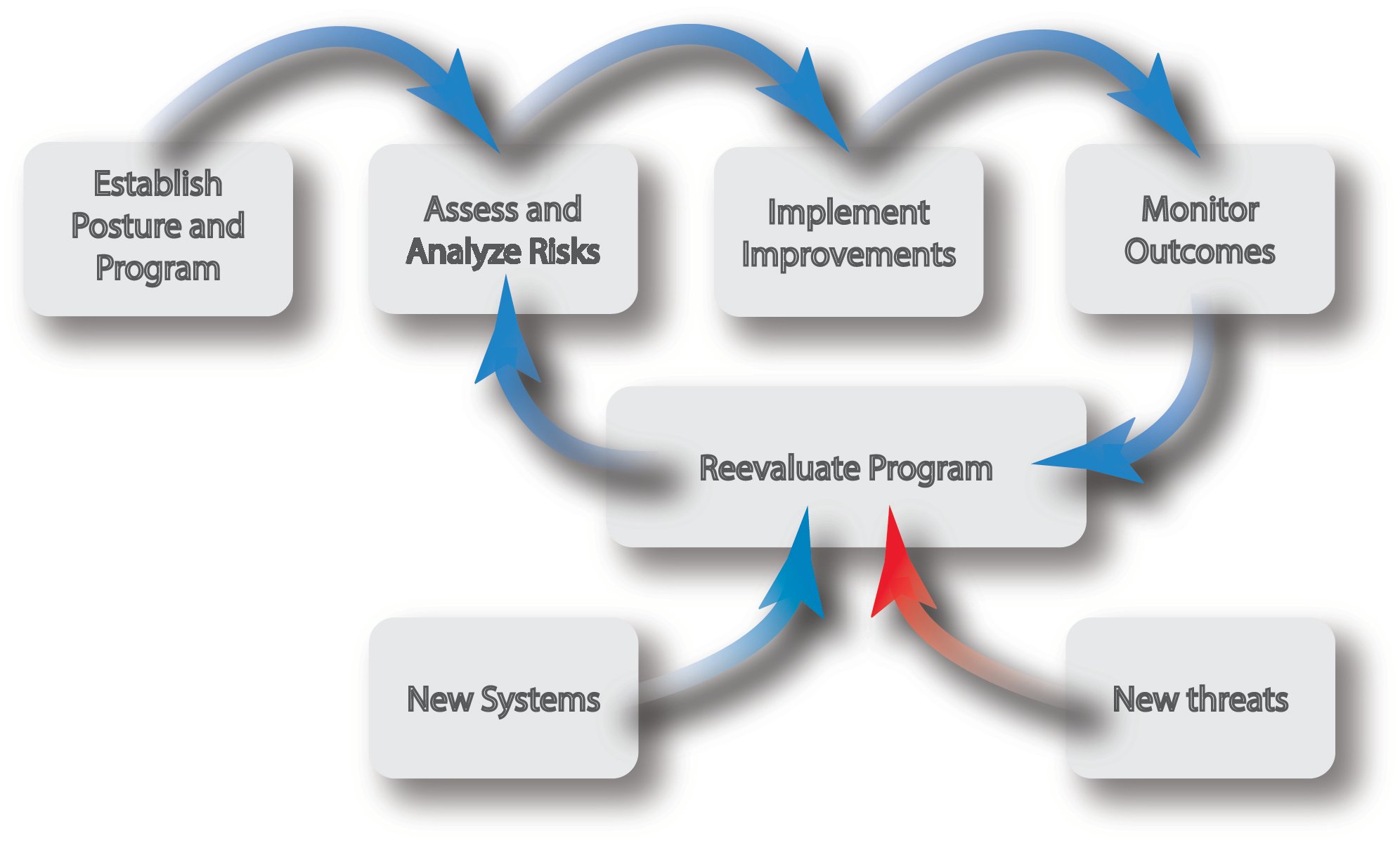
BROAD EXPERTISE AND PROVEN SOLUTIONS
Posture Assessment
It is difficult to know where to start when developing a cybersecurity strategy, and more difficult when the requirements are incompatible with the unique aspects of control systems. ACE offers cyber posture assessments to help identify your organization’s current state, and where you want to be. A posture assessment includes a review of current best practices and a collaborative workshop that focuses on the end goal of implementing the standards and strategies at the appropriate rigor for your organization. The posture assessment is a great way to align all stakeholders towards the same effort and expectations, which is the key to a successful strategy.

Writing Your Cyber Rules
When customers have requirements documentation that does not adequately address cybersecurity, projects are not implemented with your cyber posture in mind. ACE will work side-by-side with key stakeholders to advise on proper technical and organizational requirements that let work happen without opening your operation to additional cybersecurity risks. This can include creating, modifying, and updating standards and procedures.

Cybersecurity Assessment
An effective cybersecurity strategy includes reassessment throughout the lifecycle of assets, systems, and organizations. To ensure that the desired level of risk reduction is actively applied, and has not changed as systems and configurations change, ACE will perform a cybersecurity assessment on the manufacturing systems and networks to determine where they align with established requirements and specifications. ACE has experience utilizing customer frameworks and requirements or external standards such as NIST CSF. Assessment deliverables typically include a report documenting the current state, existing gaps, and prioritized recommendations for mitigating risks.
Mitigation Plans
When there are identified gaps between your target cyber posture and the realities of your current state, ACE will develop and help implement a mitigation plan to address cybersecurity weaknesses. Our remediation approach includes modifications to the system and network architecture, hardware upgrades, and mapping cybersecurity controls into software configurations. ACE understands how cyber requirements need to interact with your other process and business needs and makes accommodations for them in the final plan.

Cybersecurity Controls Implementation
You can spend hundreds of hours assessing and planning, but how do you achieve actual reduction in the cybersecurity risk to your OT assets? To reduce your organization’s attack surface and close gaps in your posture, cybersecurity countermeasures need to be applied. ACE regularly implements a wide variety of cybersecurity controls on legacy and modern OT assets, such as PLCs, HMIs, SCADA systems, PCs, servers, and networking equipment. We reduce the attack surface by applying role-based access, zone and conduit design and other techniques to assets across your control systems environment.

Cybersecurity Testing
Do you want to know that your system fully aligns with your site posture and follows policies? Even the best-intentioned implementation may miss some requirements if not verified. After implementation, site personnel periodically modify systems for troubleshooting, maintenance, and upgrade purposes. ACE tests your systems whether part of a new activity or triggered periodically according to site policies and procedures. ACE’s verification and testing services check that your installed system actually contains all the intended controls.

Related Resources
Chemicals
Project Examples
Project Example Title









.jpg)


