4 min read
Don't Let Your Remote Access Platform Be Your Cybersecurity Weakness
By: Tim Mullen on Jun 16, 2021 11:15:00 AM
Today, many critical infrastructure facilities, such as water and sewage treatment plants, have incorporated various IT remote access technologies into their industrial control systems (ICSs). While there are a number of benefits to bringing connectivity to ICS assets in these facilities, there are also numerous risks if proper cybersecurity precautions are not taken.
This was the case in February 2021 for a water treatment plant in Oldsmar, Florida. An unidentified actor used the popular remote access software TeamViewer as the pathway to launch a cyberattack against the facility. The attacker used the software to connect to the SCADA HMI PC twice in one day to command a 100-fold increase to the sodium hydroxide dosing setpoint at the plant – a potentially very dangerous level. Fortunately, in this instance the plant operators identified the irregularity immediately and were able to quickly restore operations back to normal.
Even though this is just one instance, there is a lot about ICS cybersecurity tactics, especially in relation to remote access capabilities, that we can take away from this attack. While the way TeamViewer was incorporated into the network was the root cause of this breach, there were a number of vulnerabilities identified in this facility. More specifically, investigation by the FBI and others into the facility’s cyber posture identified the following issues:
- TeamViewer was setup for direct unattended remote access
- A shared password for remote access to all PCs at the site was in use
- PCs were directly connected to the Internet without the use of a network firewall
- All PCs on site had access to the SCADA system and were using an out-of-support operating system (Windows 7)
Because there are many legitimate use cases and benefits to having remote access capabilities, the answer is not just to get rid of the capability all together unless indicated by a risk assessment. Let’s take a look at security measures that can be put into place to allow for secure remote access while providing protection from the specific attack vectors used in this case.
Tactics to Protect Your ICS when Using Remote Access Software
First and foremost, a host-based remote access solution should never be the sole layer of security between the public Internet and access to an ICS asset, which was likely the case in this instance. Figure 1 shows an example of an improper network configuration that creates cybersecurity risks for ICS assets.
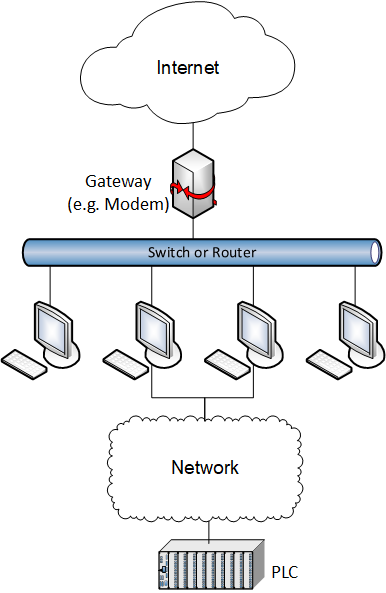
Figure 1. A diagram of a low-security configuration that poses a large risk to ICS assets.
Instead, when it is necessary to provide remote access capabilities, a defense-in-depth cybersecurity strategy must be developed that involves other security layers between the Internet and the ICS. Proper firewalling and network segmentation form parts of these layers and should prevent any remote access solutions from being directly accessible from the Internet. VPN functions should be another layer, although an assessment is required to determine the adequate level of protection for a given system. The VPN should require two-factor authentication and create a trusted pathway through which remote access capabilities can be utilized.
Beyond the firewall and VPN, the selected host-based remote access solution should be configured to provide additional layers of security in addition to providing the actual remote access services. Solutions such as TeamViewer require explicit configuration to prevent them from attempting to bypass other network security functions.
The above components should be accompanied by other recommended practices such as requiring unique, secure user credentials. For example, beyond initially granting credentials, existing credentials need to be audited and unneeded credentials revoked (such as those for employees who have left the organization) on a regular basis. Also, organizations should implement a best practice to not reuse locally managed passwords between users, apps, and devices. With readily available password management solutions today, the barriers to fixing this vulnerability are quite low.
Regarding implementing separate network zones for ICS and non-ICS applications, Figure 2 shows an improved network strategy compared to Figure 1. Depending on a risk assessment and a site’s cybersecurity posture, additional measures may be required for adequate risk reduction. Additionally, standards-setting bodies such as the National Institute of Standards and Technology (NIST), International Society of Automation (ISA), and AWWA provide guidance on how to mitigate risks of remote access solutions in ICS environments.
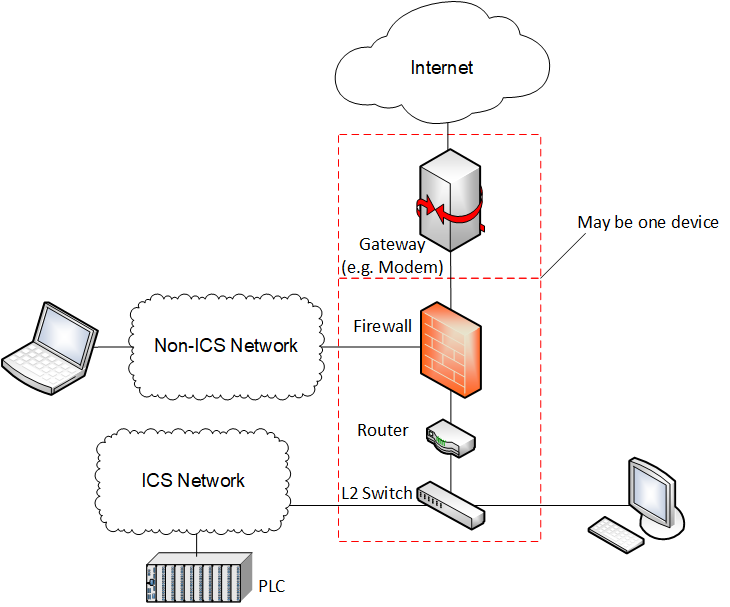
Figure 2. An example of a better ICS network configuration with layers of cybersecurity protection. If remote access capabilities are required in this network, a security device with VPN capabilities may be utilized, and appropriate configurations made on the relevant assets to add these capabilities while minimizing risk.
Prioritizing Safe and Secure Remote Access
While TeamViewer was the attack vector in this instance, the way the attack was conducted did not necessarily depend on the use of malicious software or exploitation of a security vulnerability in either TeamViewer or the host OS. This attack was accomplished using the “intended” functions of the system software. But, because of the way TeamViewer and the network were configured to provide unattended remote access to the ICS systems, exploitation of various factors such as credential reuse presented a single-link attack chain to this system. If the way this network is configured sounds like what is in place at your facility, it’s best to consult with a third-party cybersecurity expert such as ACE to prioritize hardening your system to allow for safe and secure remote access.
Learn more about our cybersecurity services and how we can help protect your valuable ICS assets
Related Posts
Five Ways to Get the Most Out of Your Control System Modernization Plan
Alarm alerts are flashing across you operator’s screen as the production line comes to a halt for...
Reverse Engineering Your Control System: Our Tips and Tricks
Your control system has been running for 25 years and it is now time to modernize. Before you can...
Implications of Log4J in your Control System
Recently across the news there has been a lot of discussion about “Log4J vulnerability” This is a...
