Threat actors looking to target your OT assets are constantly refining their processes to identify new ways to access weaknesses across your control system landscape. To prepare for this and identify cybersecurity vulnerabilities in your system, the cybersecurity policies designed to protect your programmable logic controllers (PLCs), human-machine interfaces (HMIs), and the server computers that support them need to evolve as well.

Since you likely do not have unlimited cybersecurity resources and budget, you need a method for prioritizing cybersecurity efforts. One widely adopted system in the U.S. that provides best practices for understanding, managing, and reducing cybersecurity risks is the National Institute of Standards and Technology (NIST) five-element Cybersecurity Framework pictured below.
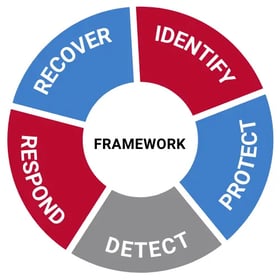 Using the NIST framework, we put together a new white paper that explores how to use your existing resources to cost-effectively assess and manage potential cybersecurity threats. In this paper we provide details on the following six low- or no-cost activities your organization should consider performing as part of the “identify” and “protect” phases of this framework:
Using the NIST framework, we put together a new white paper that explores how to use your existing resources to cost-effectively assess and manage potential cybersecurity threats. In this paper we provide details on the following six low- or no-cost activities your organization should consider performing as part of the “identify” and “protect” phases of this framework:
- Using available tools for asset identification
- Prioritizing cybersecurity efforts using a risk-based approach
- Providing integrators and OEMs with a common infrastructure
- Including cybersecurity measures in all new systems
- Reducing vulnerabilities with a defined system owner and systematic processes
- Coordinating cybersecurity efforts with existing improvement projects
We also discuss why it is imperative to select the right partner to guide you through your cybersecurity policy implementation. At ACE, we are well equipped to be this partner as our engineers have vast experience working within the NIST Cybersecurity Framework and fully understand how your OT cyber requirements must interact with your other processes and business needs.
Download our new white paper, Six Activities to Reduce the Costs of Implementing Cybersecurity Policy, to learn how you can better protect your OT assets from cyber threats with the resources you already have.



 Using the NIST framework, we put together a new white paper that explores how to use your existing resources to cost-effectively assess and manage potential cybersecurity threats. In this paper we provide details on the following six low- or no-cost activities your organization should consider performing as part of the “identify” and “protect” phases of this framework:
Using the NIST framework, we put together a new white paper that explores how to use your existing resources to cost-effectively assess and manage potential cybersecurity threats. In this paper we provide details on the following six low- or no-cost activities your organization should consider performing as part of the “identify” and “protect” phases of this framework: