PROTECT YOUR PLANT FLOOR: LAYING THE GROUNDWORK FOR EFFECTIVE CYBERSECURITY
Evaluating your organization’s cyber posture is a critical first step
Your plant floor is becoming more connected, both among devices and industrial and enterprise networks. Ensuring proper cyber protections for industrial control systems (ICSs) should be a priority for every organization.
Developing an effective ICS cybersecurity strategy requires extensive knowledge of the entire industrial control network. It's important to the success of all current and future cybersecurity projects to perform an often overlooked or misunderstood first step – assessing your organization’s cyber posture.
Evaluating your organization’s cyber posture should be the first step taken prior to developing, implementing, or even assessing your organization’s cybersecurity strategy.
By starting with a properly executed cyber posture assessment, your organization can execute the most effective cybersecurity strategy and get ahead of potentially detrimental cyber threats before they develop.
What is a Cybersecurity Posture Assessment?
A posture assessment includes a review of an organization total cybersecurity readiness. The assessment includes going over current best practices and a collaborative workshop that focuses on the end goal of implementing the standards and strategies at the appropriate rigor for your organization.
1. OT Stakeholders are not involved in the cybersecurity program development
Companies can be knee-deep in a cybersecurity implementation project yet not in agreement on what they are working towards. This generally happens because the project’s OT stakeholders were not involved in the development of the organization’s cybersecurity program. Therefore, key stakeholders are not aligned on critical parts of the program including cybersecurity standard selection, scope of applicability, agreed-upon interpretations, and acceptable and unacceptable alternative controls.
2. Auditing cybersecurity without consulting OT
When companies perform formal cybersecurity audits to determine where cyber weaknesses exist. The audit usually involves comparing systems as installed, configured, and used to a standard set of cybersecurity controls, yet the standard may not be understood or sufficiently tailored for OT.
For example, a company’s upper management might assemble a task force to perform an internal audit to assess practices at each site based on standards developed by the organization’s corporate IT group. This may inherently lead to discrepancies because each facility may not have agreed to the standards or may not be able to meet the standards with the resources they have. It may be unclear how to interpret these IT standards for OT devices.
3. Cybersecurity projects are started before establishing cybersecurity posture
It is best to perform a foundational cyber posture evaluation prior to engaging in any cybersecurity projects. If current and desired cyber posture are clearly defined first, stakeholders can work together to generate actionable and effective implementations that will reduce the risk of a cybersecurity incident.
Step 1: Information Gathering
To assess your organization's cyber posture, it is important to first gather any potentially pertinent information, including any regulatory requirements. Be sure to collect not only documented information, but also undocumented information such as tribal knowledge or ad-hoc work processes.
The information gathering process should focus on three classes of information: internal system information, internal specifications and policies, and external documentation and policies.
Internal System Information
There are two crucial pieces of information that should be looked at first in any cyber posture assessment – an asset list and network drawings and diagrams. Gaps in this documentation are indicative of an uneven cyber posture, which impact the effectiveness of any cybersecurity initiative.
The following additional internal information should also be identified at this point:
-
-
- IP addresses – A comprehensive IP address list should be included in the asset list.
- Installed software and updates – Knowing the software in use and if it is up to date is necessary for identifying critical functions of the OT system and what vulnerabilities to look for.
-
Internal Specification and Policies
It is important to look at how IT policies translate to OT SOPs. The two key policies that are crucial to the basis of step 2 are disaster recovery policies/SOPs and OT patch policies/SOPs.
SOPs for credentialing, system access, network design, cyber incident detection and response, and remote access should also be included.
External Documents and Policies
The items listed below will not be applicable to every organization, and even if something is applicable, the information might not be available, may be out of date, or could just be an ad-hoc procedure or practice. Therefore, another equally important piece of this process is simply to note when something falls into one of these categories.
-
-
- Industry best practices or requirements
- Vendor documentation/best practices for server, workstation, and network configuration
- Inventory of installed software, including version numbers
- Manufacturer support status, including costs
- Obsolescence status, including the date of any out-of-support systems
-
Step 2: Establishing Current Cyber Posture
The information gathered in step one all serve as guiding evidence for determining your organization’s current cyber posture. Establishing your organization’s current cyber posture allows you to identify the appropriate starting place for implementing effective changes that will reduce cybersecurity risks.
The process of establishing your organization’s current cyber posture is typically done in two stages. The first stage involves coordinating a brief meeting with representatives from management, operations, control system needs, regulatory compliance, and IT.
A critical goal for this team is to identify current policies and strategies in place, how these existing policies are actually being implemented, and what gaps may exist. There are numerous ways this can be done, but for simplicity, we can consider framing this conversation using ICS-CERT’s “Seven Strategies to Defend ICSs,” which include the following:
-
-
- Implement Application Whitelisting
- Ensure Proper Configuration/Patch Management
- Reduce Attack Surface Area
- Build a Defensible Environment
- Manage Authentication
- Implement Secure Remote Access
- Monitor and Respond
>>> For a deep dive into each of these strategies, download the full white paper.
-
The second part of this process involves documenting and developing a consensus on your organization’s current cyber posture. A useful tool for this assessment is to categorize the maturity of the current policies and strategies into levels that are often defined similarly to what is outlined in the table below.
|
Maturity Level
|
Policy
|
Practice |
|
Level 0
Not Started
|
The organization is not aware of this strategy. There are no written policies acknowledging security for OT. |
Cybersecure practices are not performed in regards to OT during design, procurement, or operational activities. Practices that may be defined in an IT cybersecurity program are not followed with OT. |
|
Level 1
Ad-hoc
|
Goals or guidance may be in place but may not be appropriately documented or appropriately tailored for OT. Policies may not be risk-informed. Inadequate resources or experience may exist to consider OT specifics in policy development. |
Basic cyber hygiene practices are followed at the discretion of knowledgeable individuals. Application of basic hygiene may not be consistent across the organization. IT policies may not be followed with OT. |
|
Level 2
Documented
|
Written policies exist that define goals and expectations for OT cybersecurity activities and are based on best practices. Procedures exist for implementing the policy and make this feasible for OT cybersecurity. |
Individuals execute cyber hygiene in-line with documented practices and have a sense of ownership around maintaining OT cybersecurity. |
|
Level 3
Repeatable
|
Roles are clearly assigned and adequate resources are provided to execute the program and to keep the program current. Management formally approves policies. Policies and procedures are regularly reviewed and updated. Exceptions are documented and tracked. |
Individuals are appropriately trained and consistently execute good cyber hygiene. Individuals look to find and address gaps in practice and document exceptions. Periodic tasks are executed with good regularity and these activities are verifiable. |
|
Level 4
Optimizing
|
New threats are proactively identified. Senior leadership champion and value OT cybersecurity and this is reflected in organizational culture. |
New practices are proactively researched, tested, and applied to the environment. Individuals are able to easily ascertain the risk posed by new threats and effectively respond to mitigate these risks. |
Step 3: Identifying Target Cyber Posture
Following the determination of your organization’s existing posture, an analysis should be done to establish the appropriate target posture. This analysis should identify the potential impact to business functionality from both internal and external threats and from intentional as well as unintentional actions. Based on the identified potential impacts, the organization should determine the appropriate posture needed to mitigate these risks.
If there is indeed a gap between current and desired postures, the next step is to close the gap and mitigate the identified risks. This often means planning and executing system remediation and drafting and providing training.
We know determining a cyber posture lays the groundwork for effective cyber protections, but how is this groundwork turned into effective protections?
Once your organization has established your current and target posture, the following activities should occur to reduce risk:
-
- Perform a cybersecurity assessment – Identify the gaps your organization has to meet your target cyber posture.
- Develop projects to fix gaps identified by the cybersecurity assessment – Focus on getting the right resources lined up. Prioritize where to focus resources, such as high-impact foundational gaps.
- Implement your project – With the goals clear from the outset, project implementation can focus on applying the right solutions the right way to meet the target posture.
- Review the results and use this as an opportunity to revisit your cyber posture – As projects are completed, your organization's current posture should move closer to the target posture.
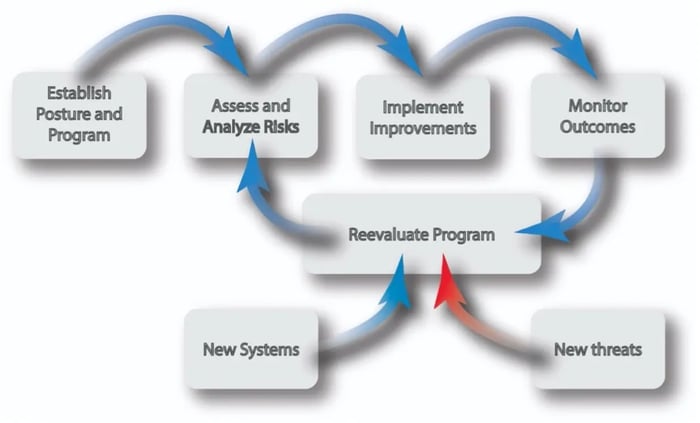
As shown above, cybersecurity is an ongoing process. This means your organization needs the right goals, tools, and support to stay effective. Cyber threats do not remain static, and neither does the OT landscape.
When your organization has an effective cyber posture, you can take the correct actions to stay abreast of evolving cyber threats.
Cybersecurity experts should initiate an open discussion or workshop about where stakeholders think the organization currently is and where they think they need to be and why.
Additionally, during the workshop, attendees should identify potential gaps and risks and what policies they believe are needed to address those. These polices should then be drafted according to a schedule agreed to at the workshop. Likewise, if policies are identified as already being in place but not being followed, this discussion can be used to determine if the policies need to be improved upon, discarded, or if more training is needed.
In some cases, during a workshop it may be determined that immediate changes can be made to improve cyber posture. You may even be able to make immediate changes, such as backing up a system. Other more time-consuming actions, such as developing an asset list or checking for vulnerabilities, can be completed after the workshop.